Cybercriminals make use of various tools that can be used to co-ordinate an attack.
Some of these tools are designed with malicious intent in mind, but research from Kaspersky’s Incident Response Analytics Report reveal that sometimes, legitimate software might have just the tool a criminal needs.
Before we continue taking a look at the software we should point out that while criminals might use this software, that’s not to say the software is inherently bad. For example, cash is incredibly useful for those without a bank account, but it’s also useful for criminals who want to avoid monitoring by banks.
With that in mind let’s look at the data.
Kaspersky says that 30 percent of all incidents it studied made use of legitimate software. Why use legitimate software? Well for one it’s easily available, the second reason is that because these tools are used widely by a number of people, malicious activity is harder to detect.
“To avoid detection and stay invisible in a compromised network for as long as possible, attackers widely use software which is developed for normal user activity, administrator tasks and system diagnostics. With these tools, attackers can gather information about corporate networks and then conduct lateral movement, change software and hardware settings or even carry out some form of malicious action,” writes head of the Global Emergency Response Team at Kaspersky, Konstantin Sapronov.
The image below from Kaspersky outlines how legitimate tools are used.
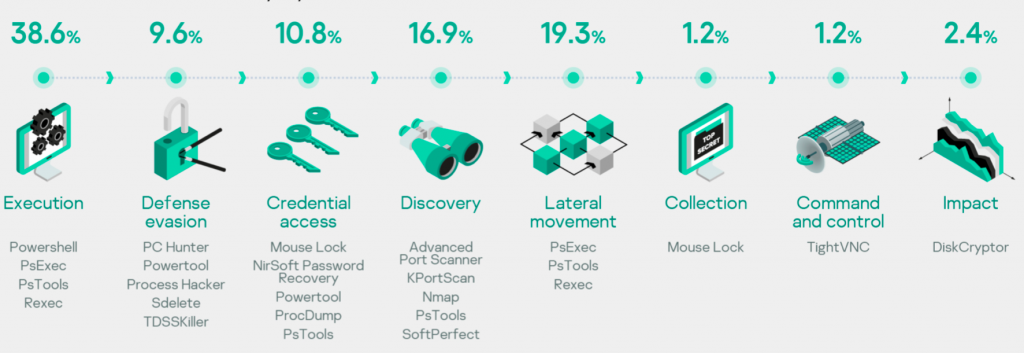
As we can see, Powershell is the most popular legitimate application to make use of because these days, what terminals don’t have it installed?
Powershell can be used for executing code, loading malware, it’s really a one stop shop and it makes sense why hackers gravitate toward it.
Another execution client, PsExec is also popular being used in 22 percent of attacks.
As for getting the lay of the land, Kaspersky found attackers using SoftPerfect Network Scanner which scans a network to reveal anything attached to it. You can even download the software for free, right now.
This application lets you see what is on a network, the MAC addresses, IP addresses and you can even SSH or FTP into a device if it’s set up to allow that.
One of the more curious tools listed by Kaspersky is Mouse Lock. This application locks your mouse to the centre of your display and dims the display.
The idea is that folks can’t use your PC when you’re away from your desk. Why an attacker might use it is beyond us.
With all of this in mind one might be wondering how to protect against threats that look like normal network traffic.
The security firm advises using a solution that offers a managed detection and response service. While there is never a guarantee that you and your firm are 100 percent safe, information is vital and managed detection and response service may help you identify a malicious individual on your network whether they’re using Powershell or something more nefarious.
[Image – CC 0 Pixabay]

